Basic Tutorial: Free Security Vulnerability Scanner ZAP

Zed Attack Proxy (ZAP) is a free and open-source web application security scanning tool developed by OWASP, a not-for-profit organization working to enhance the security of software applications. This tool is ideal for beginners to start security testing of web applications as it is easy to use, and installation is also straightforward. However, these tools are used by penetration testing professionals also. The ZAP tool is ideal for developers and functional testers to automate their applications' security testing. You can also use other tools like Selenium with ZAP to automate testing.
Stages of Application Security Assessment
Application Security assessment is a process of identifying vulnerabilities in the web application. This can be further divided into three stages:
- Reconnaissance - This is the first stage where a tester tries to extract more information related to the website. Both active and passive methods are used to gain knowledge related to software used, known vulnerabilities, hidden content, etc.
- Attack - This stage is where a tester uses different scanning tools to identify vulnerabilities in the web application. It is followed by a manual analysis of each vulnerability and identifying false positives if any.
- Report - After compiling different issues given by the scanning tool and followed by manual verification, the report is prepared and submitted to the developer to resolve those issues.
Download and Installation
ZAP is available for multiple operating systems such as Windows, MAC, and Linux. It can be downloaded free from the below link:
https://www.zaproxy.org/download/
Tool Usage
After downloading and installing, launch OWASP ZAP by clicking on the icon of ZAP.
To run the first test, just enter the URL in the field "URL to attack" (e.g. http://www.testsite.com) and click on the button "Attack". This is a basic scan and it gives security vulnerabilities.

Note: Never run this tool on any public websites as it is illegal under the law unless you have proper permission to do so.
Results
On successful running of a scan, ZAP gives the list of application security issues. All issues you can find under the tab "Alerts".

Reporting of application vulnerabilities
After the successful running of the tool, you can download reports in formats such as HTML, XML, and Markdown by navigating the ZAP tool -> Report. Also, you can also export messages, responses, and selected URLs to file in ASCII format by selecting rows under the History tab for future reference.

Configuring Proxies
You need to configure the web browser to use ZAP as a proxy. You can see these local proxy details by navigating ZAP Tool -> Tools -> Options -> Local Proxy:

You need to configure your web browser by navigating:
Firefox Menu ->Options -> Settings (Under Network Proxy) -> Manual Proxy Configuration. Set HTTP Proxy as "localhost" and Port as "8080".

You can check by browsing any URL and check whether the ZAP tool captures traffic by intercepting.
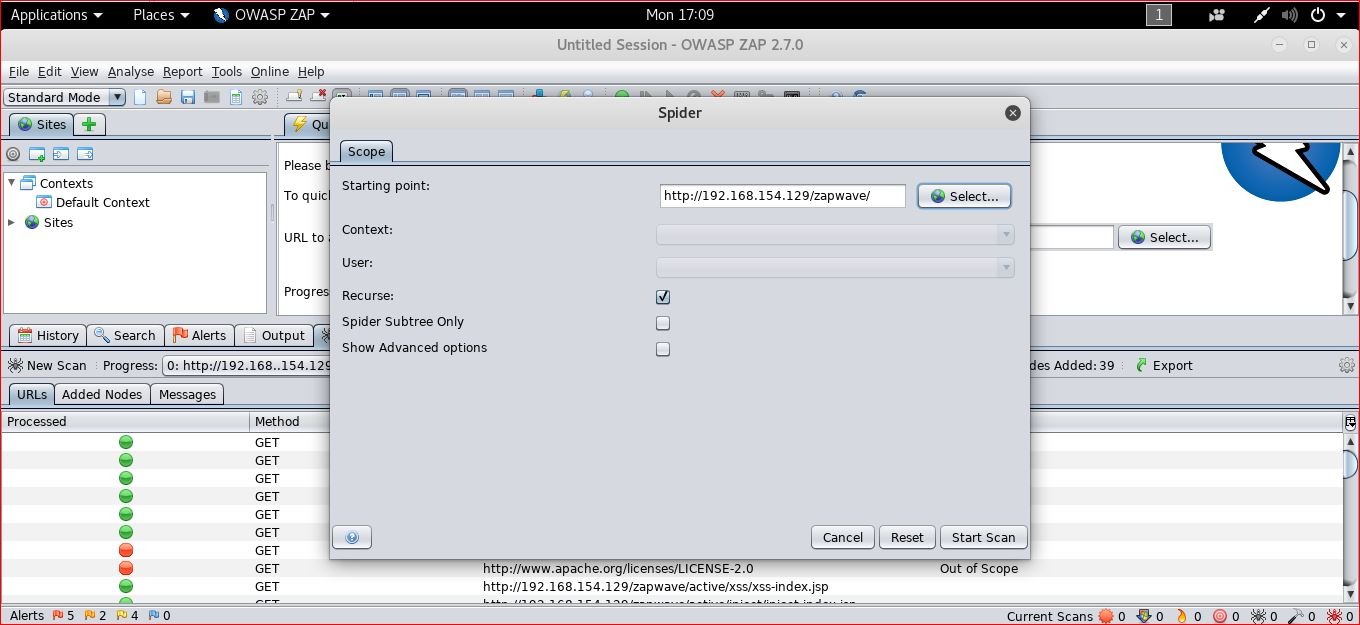
Website Crawling
For crawling the whole website automatically, you can use the Spider feature of the ZAP tool. Navigate ZAP -> Tools, click on "Spider" and enter the site URL in "Starting point".
Authentication
Some websites need usernames and passwords for vulnerability scanning. To do authentication, intercept the traffic by configuring the proxies mentioned above. Right-click on the login request, select "Flag as Context" and click "Form-based Auth Login Request".

Conclusion
OWASP ZAP is an awesome tool for beginners who wants to start a security assessment of web applications. The big community is working to enhance the features of this tool. I will definitely recommend you use this tool in your cyber security assignment.
Subscribe us to receive more such articles updates in your email.
If you have any questions, feel free to ask in the comments section below. Nothing gives me greater joy than helping my readers!
Disclaimer: This tutorial is for educational purpose only. Individual is solely responsible for any illegal act.









Nice and well structured article.
Keep posting.
I have used ZAP in application security … it is really a nice tool