Quick Tutorial: Pentest Telnet

Telnet is a network protocol and is majorly used to manage devices from a remote location. This protocol works on the server-client model. You need to have a telnet server on one system and a telnet client on other systems. Once you have set it up, you can use telnet easily. This tutorial guides you about the Telnet protocol and uses different methods used for penetration testing on telnet. Click Here to know Different Phases of Penetration Testing
Does using Telnet consider a security risk?
The short answer is a big Yes. Remember one thing, never use telnet until you have no other option. This protocol must be used as a last resort. The major reason for discouraging using telnet as it communicates all data in plain text. Assume you are managing remote devices using telnet and supply username and password. Because of design, telnet transfer username and password in plain text which is susceptible for Man in the Middle(MitM) attack.
How do attackers identify Telnet?
An attacker can use different port scanner tools to identify open ports. These tools display all open ports including telnet. The default port for telnet is 23. Although, the administrator configures it to a different port number. Still, port scanner tools are very good at finding open ports and if the telnet is open, attackers got a goldmine.
Port 23 - Telnet Vulnerabilities
- Hardcoded credentials
- Replay attack
- Sniffing attack
- Default credentials
- No authentication for access
Methods for enumerating Telnet
NMap is a popular scanner tool to identify open ports. NMap also has a set of scripts database that can be used and identify more juicy information about the target. This tool is pre-installed on Kali Linux. The below command is used to list out all available scripts related to telnet.
ls /usr/share/nmap/scripts/ | grep telnet
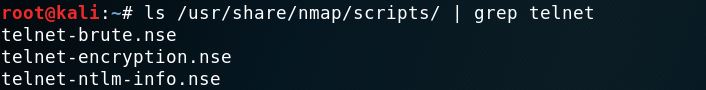
Once you identify telnet-related scripts, you can run those scripts against the target system.
nmap --script=telnet-brute.nse,telnet-encryption.nse,telnet-ntlm-info.nse <target>
(2) Banner Grabbing
If the telnet is open, an attacker can easily grab a banner that may contain sensitive information or details related to services used by your target system.
Steps:
- Open a Terminal
- Enter command: telnet <target-IP> <target-port>
- Press enter
You can use the below command to get information related to SMTP.
telnet 10.10.10.34 25
(3) Using Metasploit
You can use the Metasploit tool to enumerate Telnet. Metasploit tool is preinstalled on Kali Linux and can be launched by typing msfconsole in the Terminal.
msfconsole
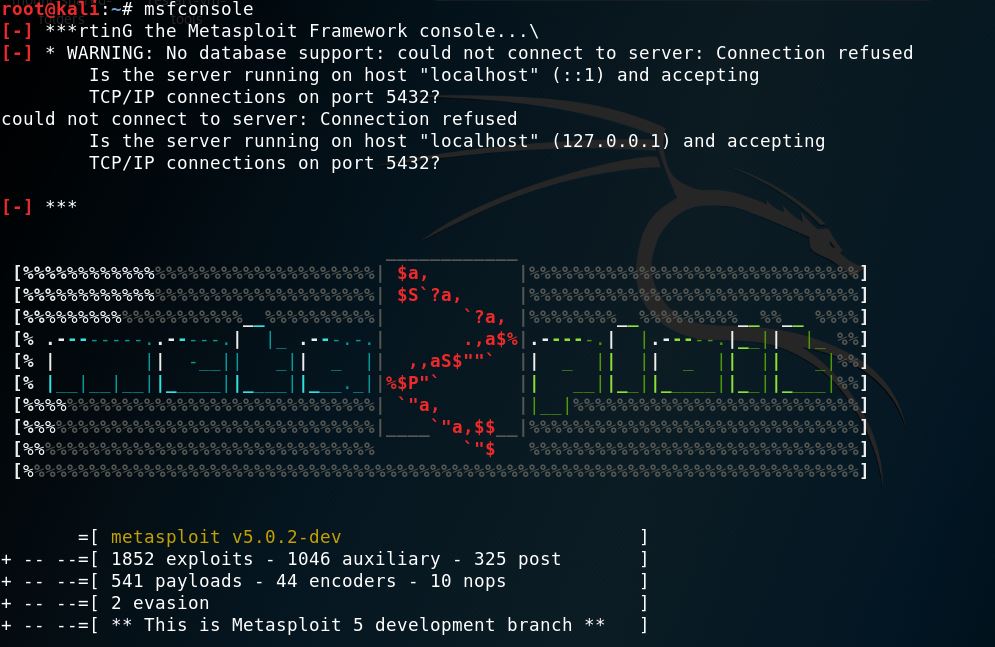
Attacker search different scanners and scripts by using the below command and running it.
search telnet

An attacker can use the Wireshark tool to further attack applications and capture the telnet traffic. By using Wireshark in between source and destination, an attacker may see usernames and passwords in plain text. Click Here to refer detailed tutorial on Wireshark.
Conclusion
This tutorial covers the telnet protocol and methods to pentest telnet by using different tools and techniques. In the end, just remember telnet provides unsecure connection and should be used only as a last resort. Use more secure protocols like SSH instead of telnet.
Subscribe us to receive more such articles updates in your email.
If you have any questions, feel free to ask in the comments section below. Nothing gives me greater joy than helping my readers!
Disclaimer: This tutorial is for educational purpose only. Individual is solely responsible for any illegal act.








