Top 10 SSH Interview Questions and Answers

SSH stands for Secure Shell which helps in connecting remote computers securely over the internet by using cryptographic techniques. It is an alternative to telnet, rlogin, and other similar protocols. Here we will discuss SSH interview questions that may be asked in an interview.
Top 10 SSH Interview Questions and Answers
Q1. What is Secure Shell (SSH)?
Ans: SSH is a network protocol that helps in accessing one desktop from another desktop securely. It helps in protecting the integrity and confidentiality of data by providing a strong encryption and authentication mechanism.
Q2. Explain briefly the uses of SSH protocol in the industry.
Ans: SSH protocol is mainly used for the remote connection of computers securely. Other usages include:
- transfer of files in a secure manner
- issuing commands to the remote host automatically
- OpenSSH may be used for connecting remote desktops without passwords
- for remote monitoring of critical infrastructure securely
- SSH protocol may be used with rsync utility for backup and transferring files on computer systems.
Q3. Which cryptography technique is used by SSH?
Ans: SSH uses symmetric, public-key cryptography and hashing techniques to authenticate the client and remote computer. AES and Blowfish are the most widely used algorithms employed in securing this protocol communication.
Q4. Which default port is used by SSH? Can we change that port? If yes, how we can change the port number of SSH?
Ans: SSH is used as the default 22 port number for communication.
Yes, we can configure the port number as per our requirements.
In Ubuntu, we need to change the default port number in the configuration file ssh_config. Navigate to /etc/ssh and edit the file with an unused port number. Save the file and restart the SSH service to take effect of the changes.
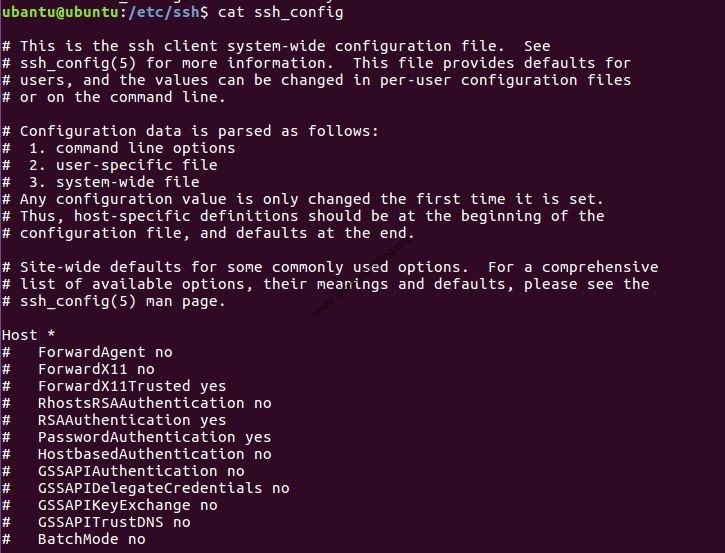
Similarly, SSH can be configured in other operating systems to change the port number in the configuration file.
Q5. How can you connect with the remote desktop with some IP? Assume you know the username and password of that machine.
Ans: Below command that may be used to connect the remote desktop.
ubantu@ubuntu:~$ssh <username>@<hostname>
<username>@<hostname>'s password: <need to enter the password>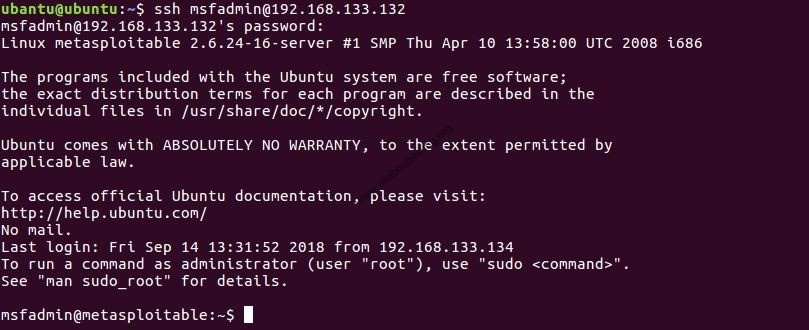
Q6. How can you run the remote commands on the target machine by using SSH?
Ans: The below command may be used to run the command on the remote machine:
ubantu@ubuntu:~$ssh <username>@<hostname> 'command'
Q7. How can we know the installed SSH version on the machine?
Ans: The below command may be used to run the command on the remote machine:
ubantu@ubuntu:~$ssh -V
Q8. Explain the working of SSH protocol.
Ans: SSH is working on the concept of the client-server model. I am listing out the steps of connecting the client with the server via SSH protocol.
- The client sends the request to the remote computer. You can consider the remote computer as a server here.
- Both the client and server agree on a large prime number(also called seed value). Also, both parties agree on an encryption generator (AES, 3DES, etc.) to manipulate the seed value.
- Both the client and server generate a private key by using another prime number independently. The public key will be generated by using the private key, encryption generator, and shared prime number independently.
- Both parties share the public key with each other. By using the public key, the client and server ensure the identity of each other by using the public key cryptography.
- Both client and server independently use the private key, the other party's public key, and the large shared prime number to generate the symmetric key.
- Once a symmetric key is generated, data will be encrypted by using it.
Q9. What is the main difference between ssh and telnet?
Ans: The basic difference between telnet and ssh protocol is that telnet connects the remote host in an unencrypted way while ssh encrypts the whole connection. Remember ssh uses port number 22 while telnet uses port number 23.
Q10. What is ssh-keygen?
Ans: It is a tool for creating the new public-private key pair for authentication. For generating, enter "sudo ssh-keygen", enter a file in which to save the key and passphrase. Below is the snapshot for the same.

Subscribe us to receive more such articles updates in your email.
If you have any questions, feel free to ask in the comments section below. Nothing gives me greater joy than helping my readers!
Disclaimer: This tutorial is for educational purpose only. Individual is solely responsible for any illegal act.








