Hack The Box Writeup - Delivery

Delivery is easy box from Hack The Box (HTB). Those who don't know, HTB is online practice platform to learn penetration testing.
Summary
- Run nmap to find open ports
- As port 80 opens, check in browser
- Click on HelpDesk and Contact Us page
- Open a new ticket on HelpDesk page
- Click on Mattermost on Contact Us page
- Sign up using @delivery.htb email address on Mattermost generated after creation of new ticket
- Check Ticket Status
- Login on Mattermost
- Use username and password to SSH
- Found user.txt
- Check config file and found mysql username, password
- Login mysql and check User table
- Found username and hashed password (bcrypt)
- Use hashcat tool to decrypt password from hash
- SSH to box and found root.txt
Start with Nmap
nmap 10.10.10.222

Run default scripts available in Nmap Database using -sC option, -sV is used to enumerate versions
nmap -sC -sV 10.10.10.222

Scan all ports with Nmap by using -p- options
nmap -p- 10.10.10.222

Run UDP scan with Nmap by using -sU option
nmap -sU 10.10.10.222

Do below entry in /etc/hosts
10.10.10.222 delivery.htb
Browse http://delivery.htb on Firefox
http://delivery.htb

Click on Contact us.
Read message on page carefully
"For unregistered users, please use our HelpDesk to get in touch with our team. Once you have an @delivery.htb email address, you'll be able to have access to our MatterMost server."

As mentioned in webpage, Click on HelpDesk.
Click on Open a New Ticket

Fill form and Create a new ticket. You received a below message after successful creation of ticket.

Click on MatterMost server. As you don't have a account, Click on Create one now. Remember to use @delivery.htb email id for creation of account.

After successful creation of account, Check status again and you got a new message.
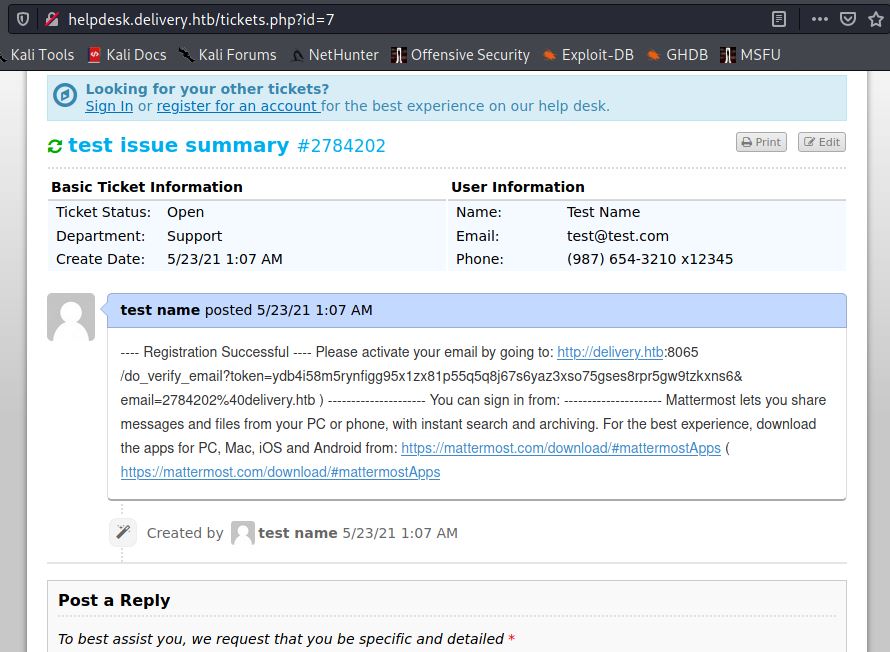
As suggest in message, activate email by copying url and paste it in browser. You got below message if you have paste correctly.

After successful login, Found credentials to the server.

As SSH port is also open, use credentials to connect remote host.
ssh maildeliverer@10.10.10.222

Just do ls and you found user.txt flag.

Privilege escalation
For privilege escalation, check config file. Config file contains a mysql username and password
Refer /opt/mattermost/config/config.json. Use below command for mysql credentials:
cat /opt/mattermost/config/config.json | grep user
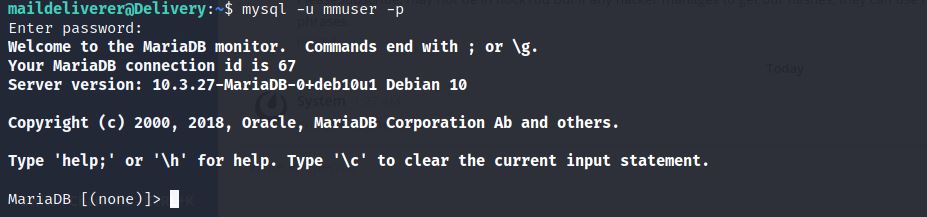
Connect mysql
mysql -u mmuser -p
Display available databases
show databases;
Use database mattermost
use mattermost;

Use below command to display tables and Users table seems to be interesting.
show tables;
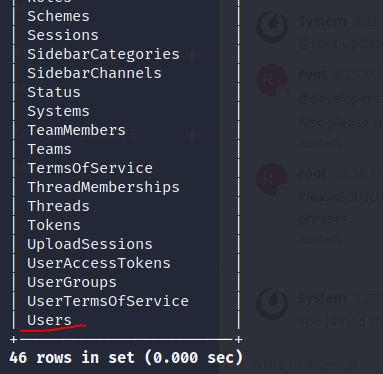
Just display username and password from table Users
select Username, Password from Users;

Save username and password in hash file. If you rehttps://allabouttesting.org/wp-content/uploads/2021/05/root-password-db.jpgfer messages, last message is saying related to password "PleaseSubscribe!"

Save it in file password.

Use hashcat command to create a wordlist and bruteforce to find match of exact password.
hashcat -m 3200 hash password --user -r /usr/share/hashcat/rules/best64.rule

Finally got matched password

Now just type su - to root
su -

Subscribe us to receive more such articles updates in your email.
If you have any questions, feel free to ask in the comments section below. Nothing gives me greater joy than helping my readers!
Disclaimer: This tutorial is for educational purpose only. Individual is solely responsible for any illegal act.








