Iptables: Quick tutorial for Beginners

Iptables is a firewall included in most Linux distributions to secure desktops from malicious requests. It can filter network packets based on the configurations. Although GUI version Firestarter is also available, iptables is also not much difficult to learn once you know the basic commands. This is a basic tutorial for beginners.
In this tutorial, we will see an installation of iptables and later some basic commands to block/allow unwanted traffic. Click Here if you are interested to learn about another Linux-based firewall, Uncomplicated firewall or ufw.
Just remember default Linux firewall is Netfilter not iptables. Netfilter is available in every Linux-based distro by default.
Advantages of iptables as a firewall
- pre-installed on most Linux-based distro
- very well documented
- absolutely free
- easy to use
- provide flexibility to set up simple rules to configure VPN
Disadvantages of using iptables as a firewall
- If you want to add any new rule to an existing iptables firewall, the entire rule needs to be reloaded.
- Not compatible with IPV6. IPV6 can be implemented using ip6tables.
Tables of iptables
| Filter table | Mangle table | Security table | Net Address Translation (NAT) table | Raw table |
| default of iptables | alter the attribute of IP headers | Mandatory Access Control (MAC) networking rules | implement NAT rules | configuring exemption in ruleset |
Installation
It is pre-installed in most Linux distributions. Although, you can install iptables by using the below command:
#sudo apt-get install iptables

To uninstall iptables, you can use the below command:
#sudo apt-get autoremove iptables

Types of chains
Iptables is categorized into three types of chains:
1) INPUT: INPUT chain is used to control the flow of incoming traffic. Suppose your friend Tom wants to SSH into your laptop, iptables use INPUT chain to match the IP address and port.
#iptables -A INPUT -s xx.xx.xx.xx -j DROP
2) OUTPUT: OUTPUT chain is used to control the outgoing flow from the machine. If you plan to ping https://allabouttesting.org, iptables will check the configuration related to the target and accordingly allow or block the connection attempt.
#iptables -A OUTPUT -s xx.xx.xx.xx -j DROP
3) FORWARD: FORWARD chain allows an administrator to control the traffic that can be routed within a LAN.
#iptables -P FORWARD DROP
Basic commands for iptables
Now we will discuss some basic commands that are frequently used by Linux users to configure iptables.
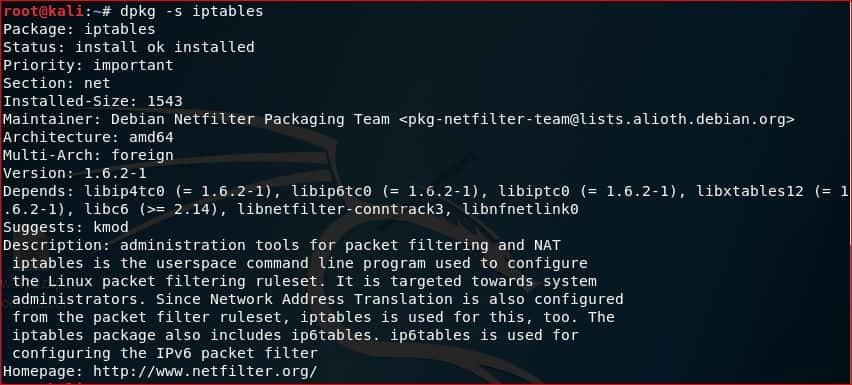
To check whether iptables is installed or not
#dpkg -s iptables
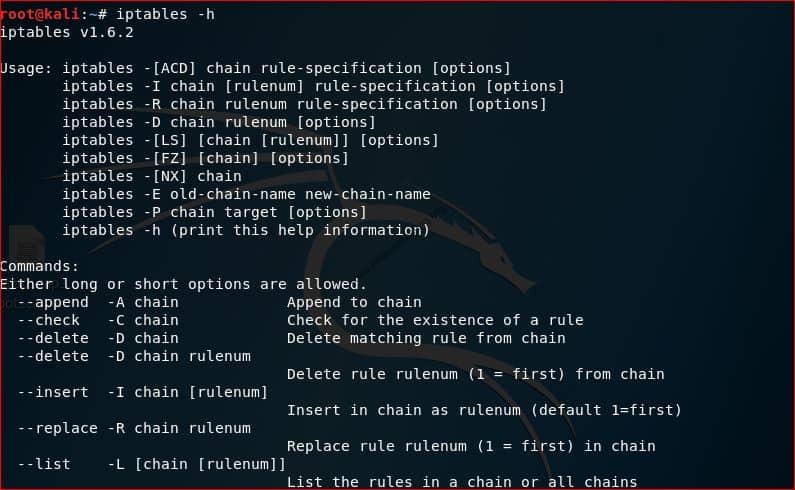
To list out all available options or commands
#iptables -h
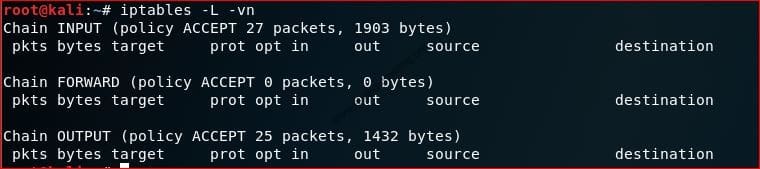
To list out all rules configured by iptables
This command lists all policies implemented by iptables. If you need to check whether iptables is blocking a port, use the below command:
#iptables -L

You can also use "#iptables -L -vn" to list out details in terms of port number, instead of its name
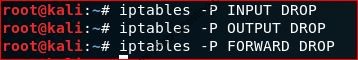
To implement a default drop policy for INPUT, OUTPUT, and FORWARD
#iptables -P INPUT DROP #iptables -P OUTPUT DROP #iptables -P FORWARD DROP
To delete/flush all rules configured by iptables
#iptables -F
Block all connections from particular IP
#iptables -A INPUT -s 192.168.0.89 -j DROP
Block all connections from a range of IPs
#iptables -A INPUT -s 192.168.0.0/24 -j DROP
Block all connections from a specific MAC address
#iptables -A INPUT -m mac --mac-source xx.xx.xx.xx.xx.xx -j DROP
Note: Use "ipconfig/all" for Windows and "ifconfig -a" for Linux to identify the machine's MAC address.
Conclusion
This is not the end of learning. Still, many more options are available to configure iptables, which helps control network packets. You can explore more to learn more features and commands of iptables.
Subscribe us to receive more such articles updates in your email.
If you have any questions, feel free to ask in the comments section below. Nothing gives me greater joy than helping my readers!
Disclaimer: This tutorial is for educational purpose only. Individual is solely responsible for any illegal act.








Nice Work..