Hash-identifier usage in Kali Linux

It is simple to use the Command Line Interface (CLI) software. It helps to identify the different types of hashes used to encrypt data, especially passwords.
You can use this tool by simply writing the below command:
#hash-identifier

Just type the hash value and this tool identifies the type of hash used to encrypt.
Examples:
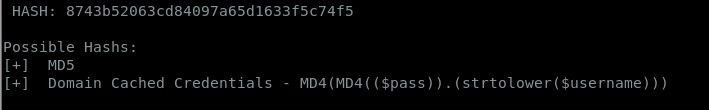
Hash: 8743b52063cd84097a65d1633f5c74f5
Type: MD5
Hash: b89eaac7e61417341b710b727768294d0e6a277b
Type: SHA-1

Hash: 7196759210defdc0
Type: MySQL323

Hash:7ca8eaaaa15eaa4c038b4c47b9313e92da827c06940e69947f85bc0fbef3eb8fd254da220ad9e208b6b28f6bb9be31dd760f1fdb26112d83f87d96b416a4d258
Type: Whirlpool

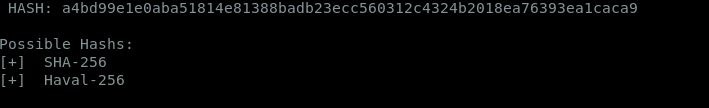
Hash:a4bd99e1e0aba51814e81388badb23ecc560312c4324b2018ea76393ea1caca9
Type: SHS-256
Subscribe us to receive more such articles updates in your email.
If you have any questions, feel free to ask in the comments section below. Nothing gives me greater joy than helping my readers!
Disclaimer: This tutorial is for educational purpose only. Individual is solely responsible for any illegal act.









bravo
how to close it!!!!!!!!!!!!!!??????
it would be nice to have a sparse output version so that one can cat a number of files and pipe it to this program to quickly see if a file contains any hashed.
Examples are great in this tutorial.
Hi to all, the contents present at this website are genuinely awesome for people experience,
well, keep up the nice work fellows.